- Home » News » World News
A third of industrial controls hit by cyber-attacks in early 2017

During the first half of 2017, the global manufacturing industry was the sector most susceptible to cyber-attacks – with the industrial control systems (ICSs) and manufacturing industry computers accounting for almost one third of all attacks, according to the cyber-security firm, Kaspersky Lab.
In a new report, Threat Landscape for Industrial Automation Systems in H1 2017, the Lab says that it detected about 18,000 different malware modifications on industrial automation systems in the first six months of 2017, by malware from more than 2,500 different families.
Also during the first half of the year, Kaspersky says that its products blocked attack attempts on 37.6% of the ICS computers from which it receives anonymised information, totalling several tens of thousands systems. This figure was 1.6% lower than in the second half of 2016.
“In the first half of the year we've seen how weakly protected industrial systems are – pretty much all of the affected industrial computers were infected accidentally and as the result of attacks targeted initially at home users and corporate networks,” says Evgeny Goncharov, head of Kaspersky Lab’s critical infrastructure defence department. “In this sense, the WannaCry and ExPetr destructive ransomware attacks proved indicative, leading to the disruption of enterprise production cycles around the world, as well as logistical failures, and forced downtime in the work of medical institutions.
“The results of such attacks can provoke intruders into further actions,” he adds. “Since we are already late with preventive measures, companies should think about proactive protective measures now to avoid ‘firefighting’ in future.”
The survey detected a peak of attack activity in March, after which the proportion of computers being attacked declined gradually from April to June.
Most of the cyber-attacks occurred in manufacturing companies that produce materials, equipment and goods. Other highly-affected sectors include engineering, education, and food & beverage. ICS computers in energy companies accounted for almost 5% of all attacks.
While the top three countries with attacked industrial computers – Vietnam (71%), Algeria (67.1%) and Morocco (65.4%) – remained the same as in Kaspersky’s previous survey, its researchers detected an increase in the percentage of systems being attacked in China (57.1%), which came in fifth.
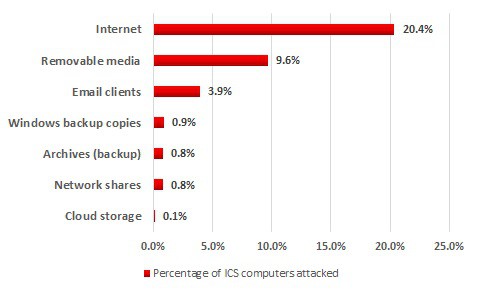
The cyber-experts also discovered that most of the attacks came via the Internet – attempts to download malware or access known malicious or phishing Web resources were blocked on 20.4% of ICS computers. They attribute this to the presence of interfaces between corporate and industrial networks, Internet access from industrial networks, and the connection of computers on industrial networks to the Internet via mobile phone networks.
In the first half of 2017, the world faced a ransomware epidemic, which also affected industrial companies. Based on the Kaspersky Lab research, the number of ICS computers attacked by encryption Trojans had tripled by June.
The experts discovered encryption ransomware belonging to 33 different families. Most of the encryption Trojans were distributed via spam emails disguised as business communications, with either malicious attachments or links to malware downloaders.
The main findings in the report related to ransomware include:
• 13.4% of all computers used in industrial infrastructure were attacked by the WannaCry ransomware;
• ICS computers in 63 countries faced numerous encryption ransomware attacks during the first half of 2017, the most notorious being the WannaCry and ExPetr campaigns, with least half of all companies in the manufacturing and oil & gas industries being attacked by the ExPetr encryption ransomware; and
• 0.5% of computers in industrial infrastructure were attacked by encryption ransomware at least once.
To protect ICS environments from possible cyber-attacks, Kaspersky recommends that users:
• take an inventory of running network services with a special emphasis on services that provide remote access to file system objects;
• audit ICS component access isolation, the network activity in their enterprise’s industrial network and at its boundaries, policies and practices related to using removable media and portable devices;
• verify the security of remote access to the industrial network as a minimum, ideally reducing or eliminating the use of remote administration tools;
• keep endpoint security systems up-to-date; and
• use advanced methods of protection that provide network traffic monitoring and the detection of cyber-attacks on industrial networks.





